Remote work
As a leading provider of security solutions, Forcepoint knows how to secure work both inside and outside the network. Learn how to adapt your security strategy to changing conditions and the transition of an increasing number of employees to remote work.
Every 5th person will permanently work remotely
According to Gartner’s survey from April 2020, this year is breakthrough in terms of changing the specifics of work. According to the survey, 74 percent of employers plan to increase the share of remote work in their organizations. At least 5 percent of on-site employees will move to remote work permanently, and nearly a quarter of enterprises will move 20 percent of their on-site employees to remote positions.
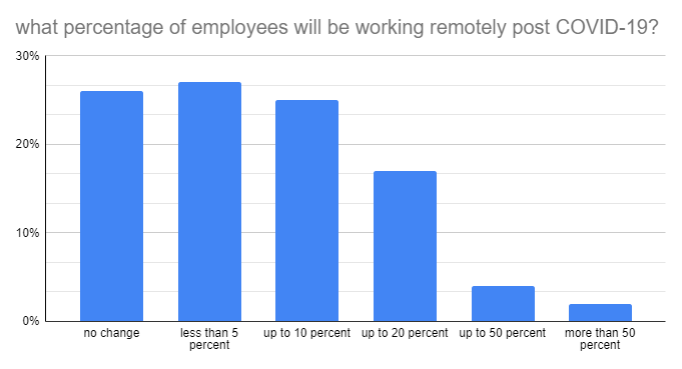
Source: Gartner, press release of 3rd April 2020, link
Forcepoint addresses the needs of the changing labor market by offering a whole spectrum of capabilities to increase the security and comfort of work.
4 pillars of secure remote work
When designing a security architecture, there are four pillars of secure remote work. Here they are:
- Secure access to company’s network
- Secure access to websites for remote workers
- Safe use of cloud applications
- Protection of critical data
1. Secure access to company’s network
Administrators have three main types of connections at their disposal:
- IPSec or SSL VPN – allow full network access, the ability to send files or directly poll machines in the environment.
- SSL VPN portal – an easier option for users. It effectively secures communication with company resources available through web browsers. Most applications provide the ability to use via the web, and thus the user does not need to install additional software on their computer to be able to work remotely safely.
- Tunneling all Internet traffic through company links – the safest solution and increasingly chosen by companies. It gives an additional layer of protection in the form of protective mechanisms operating on the company’s firewalls, such as: IPS, anti-virus or URL Filtering.
Traffic tunneling using Forcepoint Next Generation Firewall is a particularly apt choice. It is because Forcepoint NGFW is one of the most effective firewalls in the world, which have the most-developed mechanisms for securing communications in distributed networks.
2. Secure access to websites for remote workers
Employers often wonder what websites and content are accessible by their employees. They wonder if their employees are downloading any files and whether or not they are safe.
We need to remember that employees must be given secure access to websites. Of course, you can direct the company traffic through VPN and control it there using systems that are implemented in the network, but this requires directing the entire traffic through the VPN, which impacts the connection and causes high latency.
It is much more effective to implement a solution that locally secures the employees who are at the company, and direct traffic they generate when outside the company to the manufacturer’s servers in the cloud. Management and reporting in the case of such a hybrid deployment is carried out from a single console of the central management server installed in the customer’s network.
Forcepoint Web Security functionalities:
- Managing employee access to websites, in particular blocking inappropriate / unwanted websites or websites containing security threats.
- Blocking cloud applications unapproved in the company (cloud apps)
- Optional integration with the sandbox environment, which allows for identification of advanced threats by detonating suspicious files in a controlled environment — in the manufacturer’s cloud or in on-premenvironment of the Client’s network.
- inspection and management of encrypted HTTPS connections. It is so important, as encrypted traffic currently accounts for 80-90% of website inbound traffic.
- Data protection thanks to integration with Forcepoint DLP. Clients love the compact architecture of the solution and the ability to enforce DLP policies directly on the proxy server of the Web Security system.
For remote work done from home or remote company locations, hybrid deployment is an excellent solution, because central management and reporting are located in the Client’s network, while the manufacturer’s infrastructure in the cloud allows for protection without the need for a VPN connection.
3. Securing cloud applications
There are many legitimate concerns regarding the use of cloud-based applications by employees. We are talking about tools that have been approved in the organization, e.g. Office 365 or G Suite.
The solution securing employees’ access to cloud systems and applications admitted in the organization is the CASB (Cloud Access Security Broker) system, i.e. a cloud access security broker. CASB mediates between users, regardless of where they are, and cloud applications.
The most advanced solutions of this type include Forcepoint CASB, which is distinguished by integration with DLP systems, risk profile creation, API and proxy support for various types of devices and cloud monitoring.
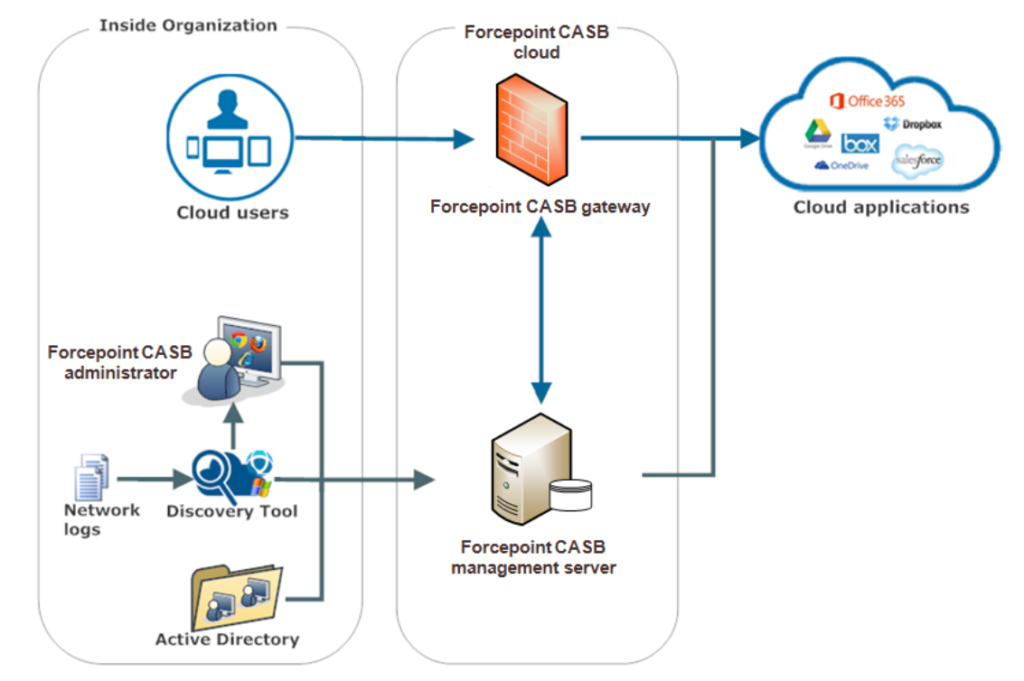
Forcepoint CASB main functionalities:
- App Discovery – analysis of what cloud applications are already being used by the employees based on logs from other systems (shadow IT)
- Controlling user access to applications (location, device, etc.)
- Controlling user activity within the application, including management of privileged users (e.g. cloud application administrators)
- Compliance management — audit of cloud application configuration vs regulations
- Detecting anomalies and threats — account takeover, etc.
- Security scanning — Advanced Malware Detection, sandboxing
- Data protection in integration with DLP, including the control of file sharing
It is also possible to protect data in the cloud by integrating CASB with DLP system, which thanks to such integration is closer to the cloud data and can monitor and control their sharing by Users.
4. CRITICAL DATA PROTECTION
What data is located on the computer of an employee working outside the office? Are there unauthorized copies of protected information on the employee’s computer? Maybe the user copied some data from the company to his private computer at home for convenience and efficiency. How is this data being used? To whom and how is it sent?
Forcepoint DLP functionalities:
- Data protection for ensuring compliance with regulations and protecting intellectual property.
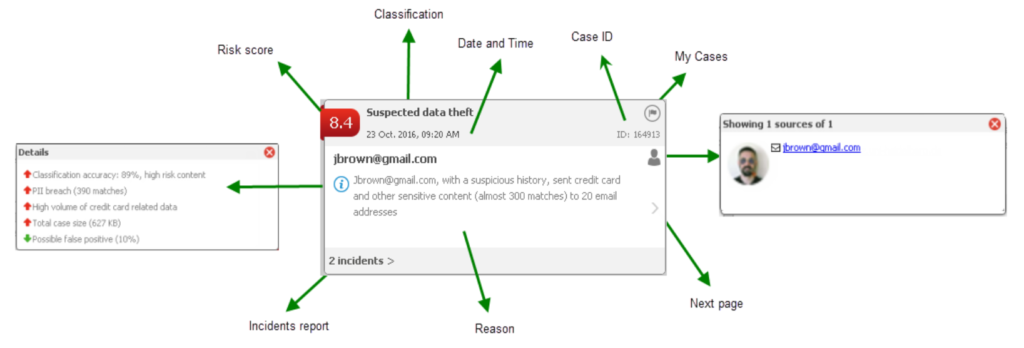
- Mechanisms supporting incident handling — Incident Risk Ranking, Force Release and E-mail Based Incident Workflow.
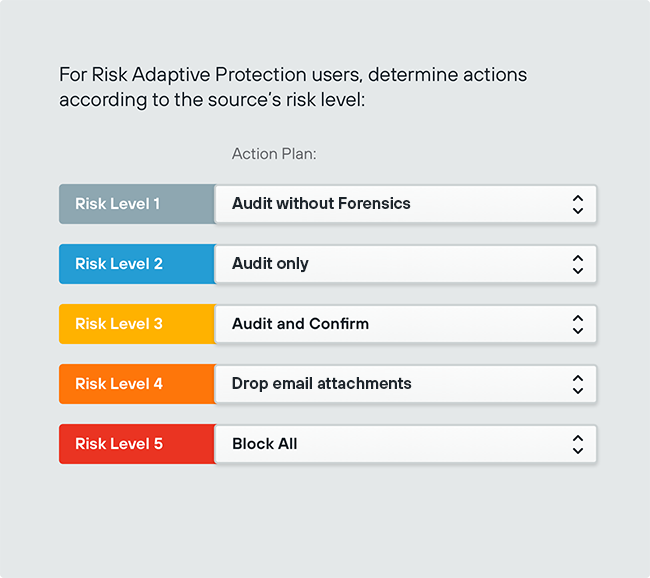
It is absolutely mandatory to secure the data located on endpoints by installing DLP Endpoint. It allows for protecting the company against unauthorized use and transfer of data by users located outside the corporate network.
DLP Endpoint is not only used for protection of employees working remotely, but also for protection during business trips or performing duties from remote, unprotected locations using a network infrastructure.
Complete and complex DLP deployment allows for the protection of data in transit, at rest and in use, using the following suites: DLP Endpoint, DLP Network, DLP Discovery and DLP Cloud Apps.
