Security
Why a traditional firewall is not enough?
- More and more contact points with Internet and its threats – thanks to the development of IT concepts such as IoT and BYOD, each office worker connects to the network using a desktop computer or laptop, telephone, often also a tablet and remotely from private devices. This means hundreds, thousands or even tens of thousands of possible security holes meaning threats such as ransomware, internet scams, password theft or phishing, and production disruptions in enterprises.
- Cloud and remote work – enabling access to the network and data for employees from anywhere creates further difficulties in monitoring access.
- More and more complicated work of network administrators – managing complex company networks, with many points of contact with Internet and the lack of full control over users’ private devices is a great challenge.
- Thousands of new malicious software every day – in 2019 350,000 new malware was created every day, which gives 4 files per second. This shows very strongly how the network attacks have changed since the 1980s and 1990s, when computers were infected for many years through one simple attack.
Forcepoint NGFW – a firewall for contemporary challenges
Forcepoint belongs to a group of the world’s most important firewall producers that protect against a whole range of threats. By combining numerous security mechanisms such as firewall, IPS, URL filtering, malware detection, protection against bypassing security systems or the most modern management console, Forcepoint ensures a peaceful sleep for administrators.
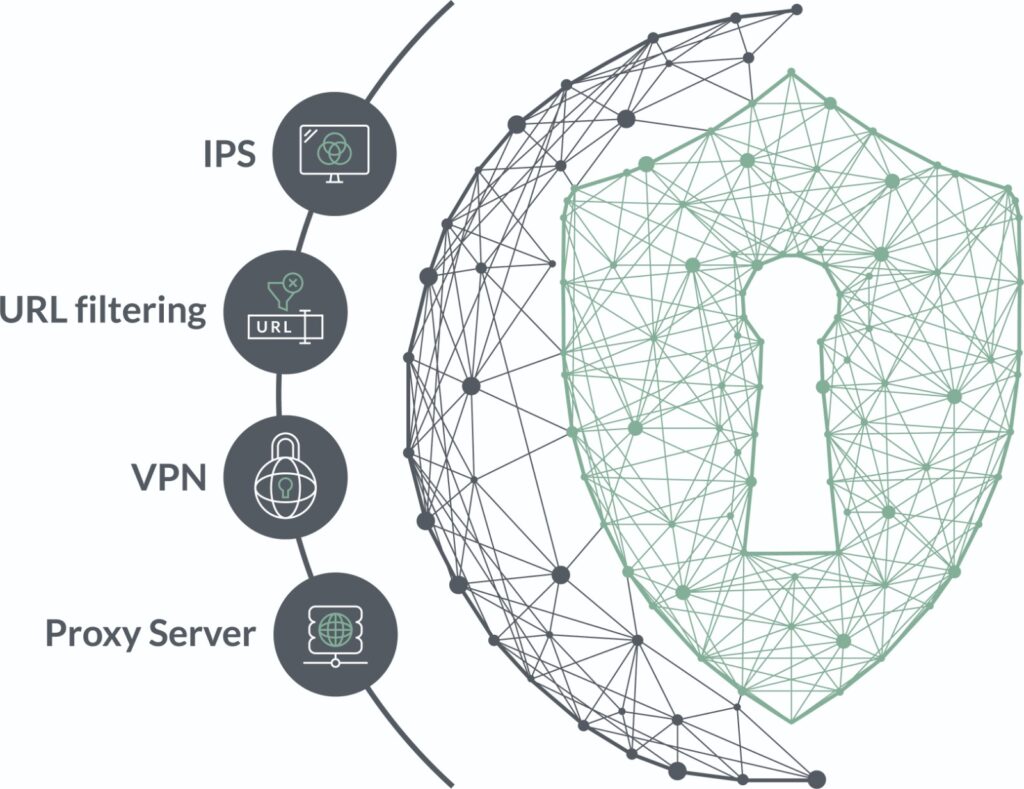
Forcepoint NGFW – built-in security functions
Forcepoint Next Generation Firewall solutions
Forcepoint Next Generation Firewall (NGFW) solutions work everywhere in the company network – from data centers, the edge of the network and company branches, to the cloud. Forcepoint NGFW was developed with performance, responsibility and security in mind.
NGFW Three families of Forcepoint NGFW platforms
Forcepoint NGFW – physical platforms
All appliances (except the 100 series) can be deployed as either a Layer 2 or Layer 3 firewall or a next generation intrusion prevention system (IPS). Most models have extensible networking interfaces (including bypass modules), which allow for configuration changes throughout the device’s life span.

6200 Series
- Ideal for data centers
- Up to 66 interfaces
- Firewall throughput 240 Gbps
- IPS & NGFW throughput 22 Gbps
- specifications

3300 Series
- Ideal for campus environments
- Up to 35 interfaces
- Firewall throughput 80-160 Gbps
- IPS & NGFW throughput 9-15 Gbps
- specifications

2100 Series
- Ideal for network edge
- Up to 28 interfaces
- Firewall throughput 60-80 Gbps
- IPS & NGFW throughput 5-7.5 Gbps
- specifications

1100 Series
- Idea for network edge
- Up to 16 interfaces
- Firewall throughput: 50-60 Gb / s
- IPS and NGFW throughput: 1.5–3 Gb / s
- specifications

300 Series
- Ideal for remote sites and branch offices (desktop design)
- 8 interfaces (2 optional modules on model 335)
- WLAN 802.11 ac/a/b/g/n optional on model 335W
- Firewall throughput 4-7 Gbps
- IPS & NGFW throughput 350-1000 Mbps
- specifications

100 Series
- Ideal for small offices or home offices (desktop design)
- 10 interfaces (8 integrated switch ports; 1 optional module on model 115)
- WLAN 802.11 ac/a/b/g/n on model 115
- Firewall throughput 1.5 Gbps
- IPS & NGFW throughput 150 Mbps
- specifications

Modular Network Interfaces
Forcepoint rack-mounted NGFWs as well as the desktop NGFW 325 and NGFW 115 accept a range of extensible network interfaces (including bypass modules that are often used with IPS), providing flexibility and adaptability to new network infrastructure. See Module Specifications for details.
Forcepoint NGFW – cloud platforms
- Unified Forcepoint NGFW software
- Problemless work in Amazon Web Services (AWS) and Azure Cloud
- Secures both north-south communication in/out of cloud and SDN east-west traffic
Forcepoint NGFW – virtual platforms
- Unified Forcepoint NGFW software
- Available for KVM and VMware ESXi and NSX
- Scales to 64 CPUs
- Automates network microsegmentation
Forcepoint IPS
What is IPS?
IPS (ang. Intrusion Prevention System) enables scanning detection, network penetration and protection against exploit attacks on server services and terminal stations. You don’t have to convince anyone that you need to protect your company’s web servers. As a business card, companies should be protected against all types of intrusion attempts. The use of the IPS system for outgoing traffic from your network is, in turn, protecting the company against possible compromise.
Currently, several dozen (!) of new malware samples are being created around the world every minute. A dynamic network traffic verification system is the only way to protect the environment against modern network attacks that bypass traditional security.
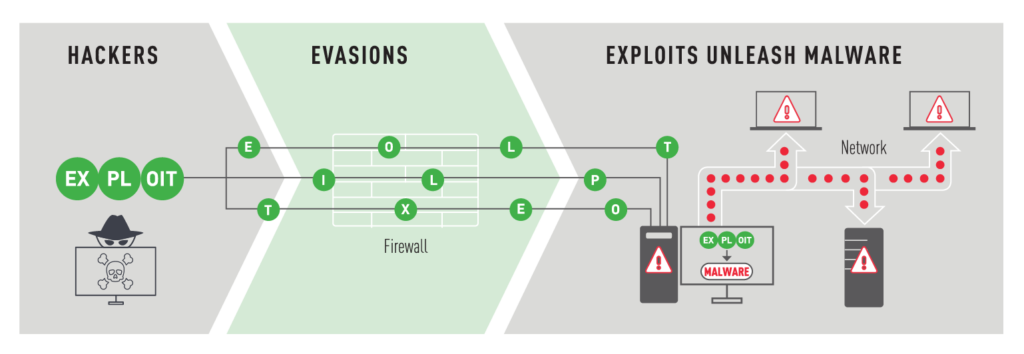
What is advanced security evasion?
Techniques for bypassing security involve changing the way information is sent across the network so that traffic can break through control systems and penetrate the enterprise network. For example, malware is divided into pieces that are sent in a disordered manner. Security not designed to protect against being bypassed does not see this shredded malware and allows confused traffic. After penetrating the network, the malicious code is again submitted to attack the internal resources of the organization.
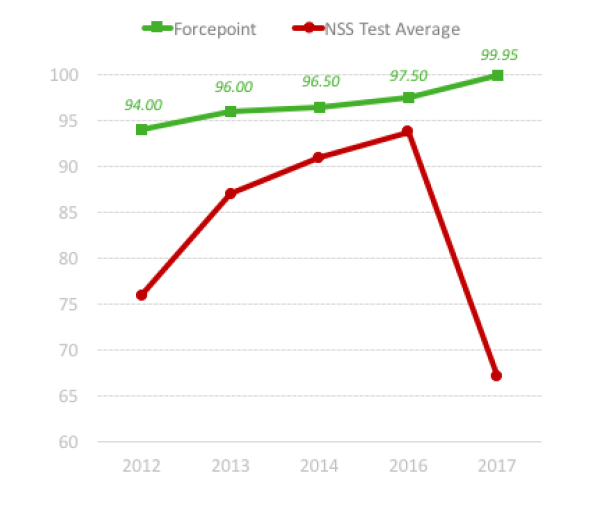
While the industry has long been aware of the hacking security techniques used, the latest next-generation firewall test by NSS Labs showed that only Forcepoint EVADER was almost 100% effective. Time to raise the bar.
Evader – stop evasions that bypass your IPS
Forcepoint Evader analyzes enterprise security against advanced attacks.
Evader consists of three elements:
- a traffic generator using security bypass techniques, i.e. simulation of attacks that could go unnoticed
- tested safety device (optional)
- vulnerable system, i.e. your company network
How Forcepoint Evader works?
Evader application can be easily configured, which allows the use of a number of flexible test sequences – from basic package modifications to more advanced attacks involving the splitting of malicious code. The graphical interface allows:
- Selection of device type to be tested.
- Choosing one of the popular exploits: MS-RPC (Conficker) or HTTP (phpBB).
- Choosing, combining and improving security bypass techniques to provide exploits; these exploits are configured only to open a harmless application window (e.g. system shell or calculator) on the target system.
- Creating and displaying reports on exploit delivery.
Evader can be run in both virtual and physical environments. It includes two static exploits and a set of techniques for bypassing dynamically selected security, which allows you to immediately and unequivocally determine whether a given security device protects against such techniques.
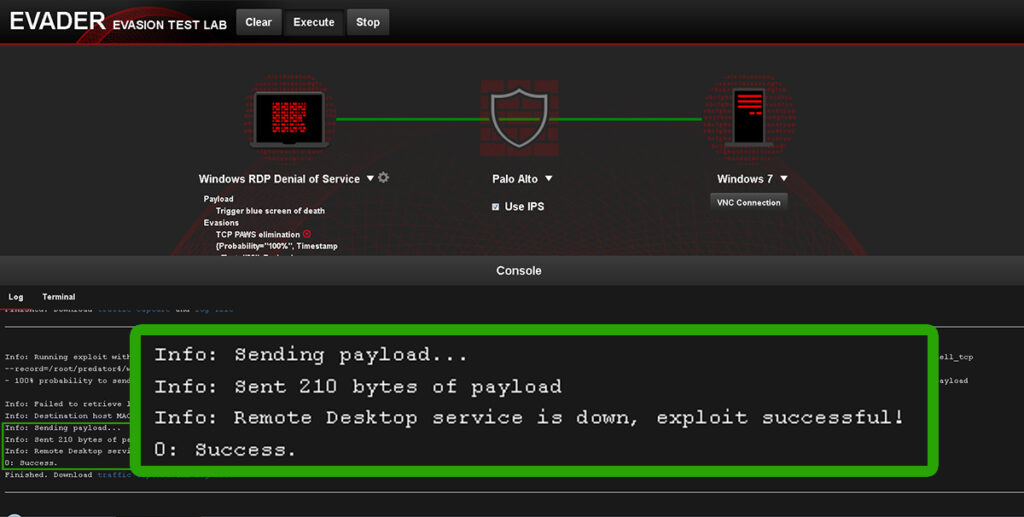
Next generation Forcepoint firewall is a pioneering solution in the field of protection against security bypass techniques. Forcepoint has spent many years improving the firewall so that it can provide unsurpassed effectiveness in neutralizing security bypass techniques. A global research team is constantly monitoring new threats and is developing new methods to protect customers.
Secure internet connection
Forcepoint URL Filtering is an extremely advanced solution that blocks access to dangerous websites and thus enables safe work.
Forcepoint URL Filtering uses ThreatSeeker Intelligence technology to collect and analyze up to 5 billion incidents (from over 155 countries) every day. As a result, URL Filtering generates current threat analyzes for Forcepoint solutions at a rate of up to 3.2 updates per second.
Forcepoint URL Filtering blocks network threats to reduce the number of malware infections, reduce the number of incidents requiring support response, and offload valuable IT resources. Forcepoint URL Filtering is an easy to implement, invisible filtering and security solution that avoids the use of complex gates with a complicated configuration.
Forcepoint URL filtering advantages
- Filtering network threats thanks to ThreatSeeker technology – identifying threats using more than 10,000 analysis techniques, machine learning and other advanced solutions maintained on a global scale in real time as part of Forcepoint Web Security
- Detailed analysis of user behavior and activity reporting – the ability to verify user activity on the network along with the ability to create reports.
- Configurable filters of allowed / forbidden URLs – temporary and / or permanent filters to manage access to websites
Eliminate malware
Forcepoint Advanced Malware Detection stops previously undetectable ransomware or other malware used in 0-day attacks before infecting your system.
Forcepoint Advanced Malware Detection
It is becoming increasingly difficult to identify malicious components of advanced threats, mainly due to the development of security evasion tactics (evasion attacks) used by cybercriminals and hostile countries. That’s why the technology for advanced malware detection – Forcepoint Advanced Malware Detection (Forcepoint AMD) was created.
Features of Forcepoint malware detection technology:
- highest accuracy – Forcepoint Advanced Malware Detection technology is unmatched in terms of protection effectiveness. Even advanced threats that are capable of bypassing security are detected by Deep Content Inspection, which tracks activity at many levels. It also controls inactive code and other indicators often overlooked by traditional sandboxing security technologies.
- no false alarms – AMD eliminates the problem of false alarms. Intervention team can devote their valuable time to responding to real threats, without the need to investigate false positives and search for violation indicators (IOC).
- easy implementation – service is an integrated module designed for Forcepoint CASB, NGFW, Web and Email Security solutions, thanks to which customers can easily activate it via cloud to obtain high availability and scalability, low maintenance costs and other advantages of the SaaS solution. AMD also allows local implementation for enterprises that do not want to use the cloud.
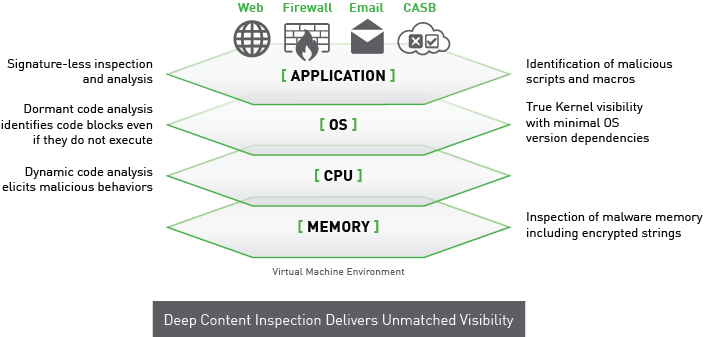
Deep Content Inspection — more than sandboxing
As with sandboxing, Forcepoint Advanced Malware Detection provides a simulated malware detection environment, but the similarities end there.
Unlike traditional sandboxes, Forcepoint AMD:
- simulates a complete environment,
- interacts with malware,
- provides complete and structured information about malware.
A complete environment
Traditional sandboxes ensure visibility only up to the level of operating system. Forcepoint, on the other hand, provides a unique isolation and controlled environment that simulates the entire host – including the processor, system memory and all devices. Deep Content Inspection interacts with malware to observe all actions, even identifies inactive code for analysis.
Interaction with malware
Only sandbox solutions create a fairly static environment, which limits the scale of malicious behaviors that can be detected. Forcepoint Advanced Malware Detection interacts with malware, therefore it is able to observe all its potential activities – even those delegated to operating system or other programs. The tool also identifies potentially harmful inactive (dormant) code that the malware does not execute.
Detailed information about malware
Related information about incidents is used to prioritize the most important threats present on the network, without having to search large log files. Full insight into the attack chain allows the intervention team to understand the nature of the attack quickly, allowing more efficient use of limited resources.
Malware detection in various channels
Cyber criminals will find and use every available environment entry point. Forcepoint Advanced Malware Detection integrates with other defense mechanisms to complement their capabilities and thwart the efforts of aggressors in many different channels. As a result, we get a shared pool of resources that improves overall visibility and strengthens every point of defense.
Forcepoint Web Security
Forcepoint Web Security is a secure Internet gateway (implemented in cloud or hybrid) that prevents advanced threats from entering the environment and blocks sensitive data leaks – regardless of whether users are in company’s headquarters, work from home or are travelling. Forcepoint Advanced Malware Detection integrates with Web Security gateway as an additional protection against zero-day malware and other advanced programs capable of bypassing security.
Forcepoint Email Security
Forcepoint Email Security blocks spam and phishing messages capable of introducing ransomware and other advanced threats into the environment before they can infect systems with malicious programs. Forcepoint Advanced Malware Detection integrates with Email Security as an additional protection against zero-day malware and other advanced programs capable of bypassing security.
Defense mechanisms of Forcepoint Email Security:
- highly effective analysis,
- URL wrapping,
- phishing education,
- advanced malware detection to protect inbound traffic,
- integrated data leakage protection for outbound traffic control
- email encryption for secure communication.
By working in industry’s most secure cloud infrastructure, Forcepoint Email Security provides unparalleled protection against phishing, malware and data leaks in Microsoft Office 365 and other popular email systems.
Forcepoint Next Generation Firewall (NGFW)
Forcepoint Next Generation Firewall (NGFW) uses many scanning techniques for files detected in network traffic, which allows administrators to tailor the security levels in detail to individual needs of each connection. Forcepoint Advanced Malware Detection integrates with Forcepoint NGFW as an additional protection against zero-day malware and other advanced programs capable of bypassing security.
Forcepoint NGFW enables to implement, monitor and update thousands of firewalls, VPNs and IPS systems from a single console, reducing network operating costs by up to 50%. The solution eliminates downtime by maintaining high availability of clusters and multi-link connections, as well as blocks attacks and manages encrypted traffic without compromising performance. As a leading product in the field of protection against advanced security bypass techniques (AET) and proxy technology for mission-critical applications, Forcepoint NGFW offers protection without any compromise.
Forcepoint CASB
Forcepoint CASB provides visibility and control over cloud-based applications, and helps eliminate security and compliance gaps in the cloud-based environment. URL filtering quickly detects prohibited applications in the cloud, and also evaluates the risks associated with them. It also allows you to assess the ability to control how legitimate cloud applications – such as Office 365, Google Suite, Salesforce, Box, Dropbox and others – are used to prevent the loss of strategic intellectual property.
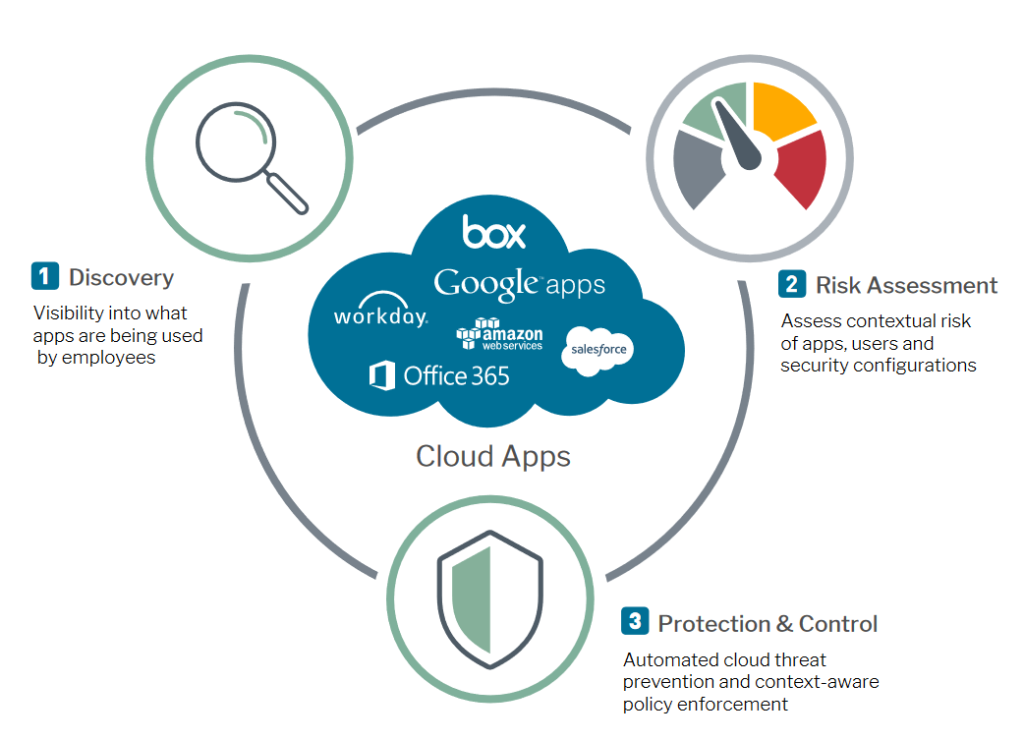
Thanks to Forcepoint CASB, enterprises can use the full potential of cloud solutions while ensuring (without causing delays) that their users do not take risky actions.
